PassLeader just published the NEWEST Fortinet NSE8_812 exam dumps! And, PassLeader offer two types of the NSE8_812 dumps — NSE8_812 VCE dumps and NSE8_812 PDF dumps, both VCE and PDF contain the NEWEST NSE8_812 exam questions, they will help you PASSING the Fortinet NSE8_812 exam easily! Now, get the NEWEST NSE8_812 dumps in VCE and PDF from PassLeader — https://www.passleader.com/nse8-812.html (60 Q&As Dumps)
What’s more, part of that PassLeader NSE8_812 dumps now are free — https://drive.google.com/drive/folders/1We0_GwUcE8mOSEjEkLplImcGPBHV5qQa
NEW QUESTION 1
SD-WAN is configured on a FortiGate. You notice that when one of the internet links has high latency the time to resolve names using DNS from FortiGate is very high. You must ensure that the FortiGate DNS resolution times are as low as possible with the least amount of work. What should you configure?
A. Configure local out traffic to use the outgoing interface based on SD-WAN rules with a manual defined IP associated to a loopback interface and configure an SD-WAN rule from the loopback to the DNS server.
B. Configure an SD-WAN rule to the DNS server and use the FortiGate interface IPs in the source address.
C. Configure two DNS servers and use DNS servers recommended by the two internet providers.
D. Configure local out traffic to use the outgoing interface based on SD-WAN rules with the interface IP and configure an SD-WAN rule to the DNS server.
Answer: D
Explanation:
SD-WAN is a feature that allows users to optimize network performance and reliability by using multiple WAN links and applying rules based on various criteria, such as latency, jitter, packet loss, etc. One way to ensure that the FortiGate DNS resolution times are as low as possible with the least amount of work is to configure local out traffic to use the outgoing interface based on SD-WAN rules with the interface IP and configure an SD-WAN rule to the DNS server. This means that the FortiGate will use the best WAN link available to send DNS queries to the DNS server according to the SD-WAN rule, and use its own interface IP as the source address. This avoids NAT issues and ensures optimal DNS performance.
https://docs.fortinet.com/document/fortigate/7.0.0/sd-wan/19662/sd-wan
NEW QUESTION 2
A retail customer with a FortiADC HA cluster load balancing five webservers in L7 Full NAT mode is receiving reports of users not able to access their website during a sale event. But for clients that were able to connect, the website works fine. CPU usage on the FortiADC and the web servers is low, application and database servers are still able to handle more traffic, and the bandwidth utilization is under 30%. Which two options can resolve this situation? (Choose two.)
A. Change the persistence rule to LB_PERSIS_SSL_SESSJD.
B. Add more web servers to the real server poof.
C. Disable SSL between the FortiADC and the web servers.
D. Add a connection-pool to the FortiADC virtual server.
Answer: BD
Explanation:
Option B: Adding more web servers to the real server pool will increase the overall capacity of the load balancer, which should help to resolve the issue of users not being able to access the website.
Option D: Adding a connection-pool to the FortiADC virtual server will allow the load balancer to cache connections to the web servers, which can help to improve performance and reduce the number of dropped connections.
Option A: Changing the persistence rule to LB_PERSIS_SSL_SESSJD would only be necessary if the current persistence rule is not working properly. In this case, the CPU usage on the FortiADC and the web servers is low, so the persistence rule is likely not the issue.
Option C: Disabling SSL between the FortiADC and the web servers would reduce the load on the FortiADC, but it would also make the website less secure. Since the bandwidth utilization is under 30%, it is unlikely that disabling SSL would resolve the issue.
https://docs.fortinet.com/document/fortiadc/7.2.1/handbook/970956/configuring-virtual-servers
NEW QUESTION 3
Which feature must you enable on the BGP neighbors to accomplish this goal?
A. Graceful-restart
B. Deterministic-med
C. Synchronization
D. Soft-reconfiguration
Answer: A
Explanation:
Graceful-restart is a feature that allows BGP neighbors to maintain their routing information during a BGP restart or failover event, without disrupting traffic forwarding or causing route flaps. Graceful- restart works by allowing a BGP speaker (the restarting router) to notify its neighbors (the helper routers) that it is about to restart or failover, and request them to preserve their routing information and forwarding state for a certain period of time (the restart time). The helper routers then mark the routes learned from the restarting router as stale, but keep them in their routing table and continue forwarding traffic based on them until they receive an end-of-RIB marker from the restarting router or until the restart time expires. This way, graceful-restart can minimize traffic disruption and routing instability during a BGP restart or failover event.
https://docs.fortinet.com/document/fortigate/7.0.0/cookbook/19662/bgp-graceful-restart
NEW QUESTION 4
You are responsible for recommending an adapter type for NICs on a FortiGate VM that will run on an ESXi Hypervisor. Your recommendation must consider performance as the main concern, cost is not a factor. Which adapter type for the NICs will you recommend?
A. Native ESXi Networking with E1000
B. Virtual Function (VF) PCI Passthrough
C. Native ESXi Networking with VMXNET3
D. Physical Function (PF) PCI Passthrough
Answer: C
Explanation:
The FortiGate VM is a virtual firewall appliance that can run on various hypervisors, such as ESXi, Hyper-V, KVM, etc. The adapter type for NICs on a FortiGate VM determines the performance and compatibility of the network interface cards with the hypervisor and the physical network. There are different adapter types available for NICs on a FortiGate VM, such as E1000, VMXNET3, SR-IOV, etc. If performance is the main concern and cost is not a factor, one option is to use native ESXi networking with VMXNET3 adapter type for NICs on a FortiGate VM that will run on an ESXi hypervisor. VMXNET3 is a paravirtualized network interface card that is optimized for performance in virtual machines and supports features such as multiqueue support, Receive Side Scaling (RSS), Large Receive Offload (LRO), IPv6 offloads, and MSI/MSI-X interrupt delivery. Native ESXi networking means that the FortiGate VM uses the standard virtual switch (vSwitch) or distributed virtual switch (dvSwitch) provided by the ESXi hypervisor to connect to the physical network. This option can provide high performance and compatibility for NICs on a FortiGate VM without requiring additional hardware or software components.
https://docs.fortinet.com/document/fortigate/7.0.0/vm-installation-for-vmware-esxi/19662/installing-fortigate-vm-on-vmware-esxi
https://docs.fortinet.com/document/fortigate/7.0.0/vm-installation-for-vmware-esxi/19662/networking
NEW QUESTION 5
You are deploying a FortiExtender (FEX) on a FortiGate-60F. The FEX will be managed by the FortiGate. You anticipate high utilization. The requirement is to minimize the overhead on the device for WAN traffic. Which action achieves the requirement in this scenario?
A. Add a switch between the FortiGate and FEX.
B. Enable CAPWAP connectivity between the FortiGate and the FortiExtender.
C. Change connectivity between the FortiGate and the FortiExtender to use VLAN Mode.
D. Add a VLAN under the FEX-WAN interface on the FortiGate.
Answer: C
Explanation:
VLAN Mode is a more efficient way to connect a FortiExtender to a FortiGate than CAPWAP Mode. This is because VLAN Mode does not require the FortiExtender to send additional control traffic to the FortiGate. The other options are not correct:
Option A: Add a switch between the FortiGate and FEX. This will add overhead to the network, as the switch will need to process the traffic.
Option B: Enable CAPWAP connectivity between the FortiGate and the FortiExtender. This will increase the overhead on the FortiGate, as it will need to process additional control traffic.
Option D: Add a VLAN under the FEX-WAN interface on the FortiGate. This will not affect the overhead on the FortiGate.
NEW QUESTION 6
You want to use the MTA adapter feature on FortiSandbox in an HA-Cluster. Which statement about this solution is true?
A. The configuration of the MTA Adapter Local Interface is different than on port1.
B. The MTA adapter is only available in the primary node.
C. The MTA adapter mode is only detection mode.
D. The configuration is different than on a standalone device.
Answer: B
Explanation:
The MTA adapter feature on FortiSandbox is a feature that allows FortiSandbox to act as a mail transfer agent (MTA) that can receive, inspect, and forward email messages from external sources. The MTA adapter feature can be used to integrate FortiSandbox with third-party email security solutions that do not support direct integration with FortiSandbox, such as Microsoft Exchange Server or Cisco Email Security Appliance (ESA). The MTA adapter feature can also be used to enhance email security by adding an additional layer of inspection and filtering before delivering email messages to the final destination. The MTA adapter feature can be enabled on FortiSandbox in an HA-Cluster, which is a configuration that allows two FortiSandbox units to synchronize their settings and data and provide high availability and load balancing for sandboxing services. However, one statement about this solution that is true is that the MTA adapter is only available in the primary node. This means that only one FortiSandbox unit in the HA-Cluster can act as an MTA and receive email messages from external sources, while the other unit acts as a backup node that can take over the MTA role if the primary node fails or loses connectivity. This also means that only one IP address or FQDN can be used to configure the external sources to send email messages to the FortiSandbox MTA, which is the IP address or FQDN of the primary node.
https://docs.fortinet.com/document/fortisandbox/3.2.0/administration-guide/19662/mail-transfer-agent-mta
https://docs.fortinet.com/document/fortisandbox/3.2.0/administration-guide/19662/high-availability-ha
NEW QUESTION 7
You are migrating the branches of a customer to FortiGate devices. They require independent routing tables on the LAN side of the network. After reviewing the design, you notice the firewall will have many BGP sessions as you have two data centers (DC) and two ISPs per DC while each branch is using at least 10 internal segments. Based on this scenario, what would you suggest as the more efficient solution, considering that in the future the number of internal segments, DCs or internet links per DC will increase?
A. No change in design is needed as even small FortiGate devices have a large memory capacity.
B. Acquire a FortiGate model with more capacity, considering the next 5 years growth.
C. Implement network-id, neighbor-group and increase the advertisement-interval.
D. Redesign the SD-WAN deployment to only use a single VPN tunnel and segment traffic using VRFs on BGP.
Answer: D
Explanation:
Using multiple VPN tunnels and BGP sessions for each internal segment is not scalable and efficient, especially when the number of segments, DCs or internet links per DC increases. A better solution is to use a single VPN tunnel per branch and segment traffic using virtual routing and forwarding (VRF) instances on BGP. This way, each VRF can have its own routing table and BGP session, while sharing the same VPN tunnel.
https://docs.fortinet.com/document/fortigate/6.4.0/cookbook/103439/sd-wan-with-vrf-and-bgp
NEW QUESTION 8
A customer is planning on moving their secondary data center to a cloud-based laaS. They want to place all the Oracle-based systems Oracle Cloud, while the other systems will be on Microsoft Azure with ExpressRoute service to their main data center. They have about 200 branches with two internet services as their only WAN connections. As a security consultant you are asked to design an architecture using Fortinet products with security, redundancy and performance as a priority. Which two design options are true based on these requirements? (Choose two.)
A. Systems running on Azure will need to go through the main data center to access the services on Oracle Cloud.
B. Use FortiGate VM for IPSEC over ExpressRoute, as traffic is not encrypted by Azure.
C. Branch FortiGate devices must be configured as VPN clients for the branches’ internal network to be able to access Oracle services without using public IPs.
D. Two ExpressRoute services to the main data center are required to implement SD-WAN between a FortiGate VM in Azure and a FortiGate device at the data center edge.
Answer: AC
Explanation:
Option A: Systems running on Azure will need to go through the main data center to access the services on Oracle Cloud. This is because the Oracle Cloud is not directly connected to the Azure Cloud. The traffic will need to go through the main data center in order to reach the Oracle Cloud.
Option C: Branch FortiGate devices must be configured as VPN clients for the branches’ internal network to be able to access Oracle services without using public IPs. This is because the Oracle Cloud does not allow direct connections from the internet. The traffic will need to go through the FortiGate devices in order to reach the Oracle Cloud.
The other options are not correct:
Option B: Use FortiGate VM for IPSEC over ExpressRoute, as traffic is not encrypted by Azure. This is not necessary. Azure does encrypt traffic over ExpressRoute.
Option D: Two ExpressRoute services to the main data center are required to implement SD-WAN between a FortiGate VM in Azure and a FortiGate device at the data center edge. This is not necessary. A single ExpressRoute service can be used to implement SD-WAN between a FortiGate VM in Azure and a FortiGate device at the data center edge.
NEW QUESTION 9
Which two statements are correct on a FortiGate using the FortiGuard Outbreak Protection Service (VOS)? (Choose two.)
A. The FortiGuard VOS can be used only with proxy-base policy inspections.
B. If third-party AV database returns a match the scanned file is deemed to be malicious.
C. The antivirus database queries FortiGuard with the hash of a scanned file.
D. The AV engine scan must be enabled to use the FortiGuard VOS feature.
E. The hash signatures are obtained from the FortiGuard Global Threat Intelligence database.
Answer: CE
Explanation:
Option C: The antivirus database queries FortiGuard with the hash of a scanned file. This is how the FortiGuard VOS service works. The FortiGate queries FortiGuard with the hash of a scanned file, and FortiGuard returns a list of known malware signatures that match the hash.
Option E: The hash signatures are obtained from the FortiGuard Global Threat Intelligence database. This is where the FortiGuard VOS service gets its hash signatures from. The FortiGuard Global Threat Intelligence database is updated regularly with new malware signatures.
NEW QUESTION 10
A remote worker requests access to an SSH server inside the network. You deployed a ZTNA Rule to their FortiClient. You need to follow the security requirements to inspect this traffic. Which two statements are true regarding the requirements? (Choose two.)
A. FortiGate can perform SSH access proxy host-key validation.
B. You need to configure a FortiClient SSL-VPN tunnel to inspect the SSH traffic.
C. SSH traffic is tunneled between the client and the access proxy over HTTPS.
D. Traffic is discarded as ZTNA does not support SSH connection rules.
Answer: AC
Explanation:
ZTNA supports SSH connection rules that allow remote workers to access SSH servers inside the network through an HTTPS tunnel between the client and the access proxy (FortiGate). The access proxy acts as an SSH client to connect to the real SSH server on behalf of the user, and performs host-key validation to verify the identity of the server. The user can use any SSH client that supports HTTPS proxy settings, such as PuTTY or OpenSSH.
https://docs.fortinet.com/document/fortigate/7.0.0/ztna-deployment/899992/configuring-ztna-rules-to-control-access
NEW QUESTION 11
A customer’s cybersecurity department needs to implement security for the traffic between two VPCs in AWS, but these belong to different departments within the company. The company uses a single region for all their VPCs. Which two actions will achieve this requirement while keeping separate management of each department’s VPC? (Choose two.)
A. Create a transit VPC with a FortiGate HA cluster, connect to the other two using VPC peering, and use routing tables to force traffic through the FortiGate cluster.
B. Create an 1AM account for the cybersecurity department to manage both existing VPC, create a FortiGate HA Cluster on each VPC and IPSEC VPN to force traffic between the VPCs through the FortiGate clusters.
C. Migrate all the instances to the same VPC and create 1AM accounts for each department, then implement a new subnet for a FortiGate auto-scaling group and use routing tables to force the traffic through the FortiGate cluster.
D. Create a VPC with a FortiGate auto-scaling group with a Transit Gateway attached to the three VPC to force routing through the FortiGate cluster.
Answer: AD
Explanation:
To implement security for the traffic between two VPCs in AWS, while keeping separate management of each department’s VPC, two possible actions are:
– Create a transit VPC with a FortiGate HA cluster, connect to the other two using VPC peering, and use routing tables to force traffic through the FortiGate cluster. This option allows the cybersecurity department to manage the transit VPC and apply security policies on the FortiGate cluster, while the other departments can manage their own VPCs and instances. The VPC peering connections enable direct communication between the VPCs without using public IPs or gateways. The routing tables can be configured to direct all inter-VPC traffic to the transit VPC.
– Create a VPC with a FortiGate auto-scaling group with a Transit Gateway attached to the three VPCs to force routing through the FortiGate cluster. This option also allows the cybersecurity department to manage the security VPC and apply security policies on the FortiGate cluster, while the other departments can manage their own VPCs and instances. The Transit Gateway acts as a network hub that connects multiple VPCs and on-premises networks. The routing tables can be configured to direct all inter-VPC traffic to the security VPC.
https://docs.fortinet.com/document/fortigate-public-cloud/7.2.0/aws-administration-guide/506140/connecting-a-local-fortigate-to-an-aws-vpc-vpn
https://docs.fortinet.com/document/fortigate-public-cloud/7.0.0/sd-wan-architecture-for-enterprise/166334/sd-wan-configuration
NEW QUESTION 12
A customer with a FortiDDoS 200F protecting their fibre optic internet connection from incoming traffic sees that all the traffic was dropped by the device even though they were not under a DoS attack. The traffic flow was restored after it was rebooted using the GUI. Which two options will prevent this situation in the future? (Choose two.)
A. Change the Adaptive Mode.
B. Create an HA setup with a second FortiDDoS 200F.
C. Move the internet connection from the SFP interfaces to the LC interfaces.
D. Replace with a FortiDDoS 1500F.
Answer: BD
Explanation:
Option B is correct because creating an HA setup with a second FortiDDoS 200F will provide redundancy in case one of the devices fails. This will prevent all traffic from being dropped in the event of a failure.
Option D is correct because the FortiDDoS 1500F has a larger throughput capacity than the FortiDDoS 200F. This means that it will be less likely to drop traffic even under heavy load.
Option A is incorrect because changing the Adaptive Mode will not prevent the device from dropping traffic.
Option C is incorrect because moving the internet connection from the SFP interfaces to the LC interfaces will not change the throughput capacity of the device.
NEW QUESTION 13
You must configure an environment with dual-homed servers connected to a pair of FortiSwitch units using an MCLAG. Multicast traffic is expected in this environment, and you should ensure unnecessary traffic is pruned from links that do not have a multicast listener. In which two ways must you configure the igmps-f lood-traffic and igmps-flood-report settings? (Choose two.)
A. disable on ICL trunks
B. enable on ICL trunks
C. disable on the ISL and FortiLink trunks
D. enable on the ISL and FortiLink trunks
Answer: AD
Explanation:
To ensure that unnecessary multicast traffic is pruned from links that do not have a multicast listener, you must disable IGMP flood traffic on the ICL trunks and enable IGMP flood reports on the ISL and FortiLink trunks. Disabling IGMP flood traffic will prevent the FortiSwitch units from flooding multicast traffic to all ports on the ICL trunks. This will help to reduce unnecessary multicast traffic on the network. Enabling IGMP flood reports will allow the FortiSwitch units to learn which ports are interested in receiving multicast traffic. This will help the FortiSwitch units to prune multicast traffic from links that do not have a multicast listener.
NEW QUESTION 14
Refer to the exhibit showing the history logs from a FortiMail device:

Which FortiMail email security feature can an administrator enable to treat these emails as spam?
A. DKIM validation in a session profile.
B. Sender domain validation in a session profile.
C. Impersonation analysis in an antispam profile.
D. Soft fail SPF validation in an antispam profile.
Answer: C
Explanation:
Impersonation analysis is a feature that detects emails that attempt to impersonate a trusted sender, such as a company executive or a well-known brand, by using spoofed or look-alike email addresses. This feature can help prevent phishing and business email compromise (BEC) attacks. Impersonation analysis can be enabled in an antispam profile and applied to a firewall policy.
https://docs.fortinet.com/document/fortimail/6.4.0/administration-guide/103663/impersonation-analysis
NEW QUESTION 15
Refer to the exhibit, which shows the high availability configuration for the FortiAuthenticator (FAC1):
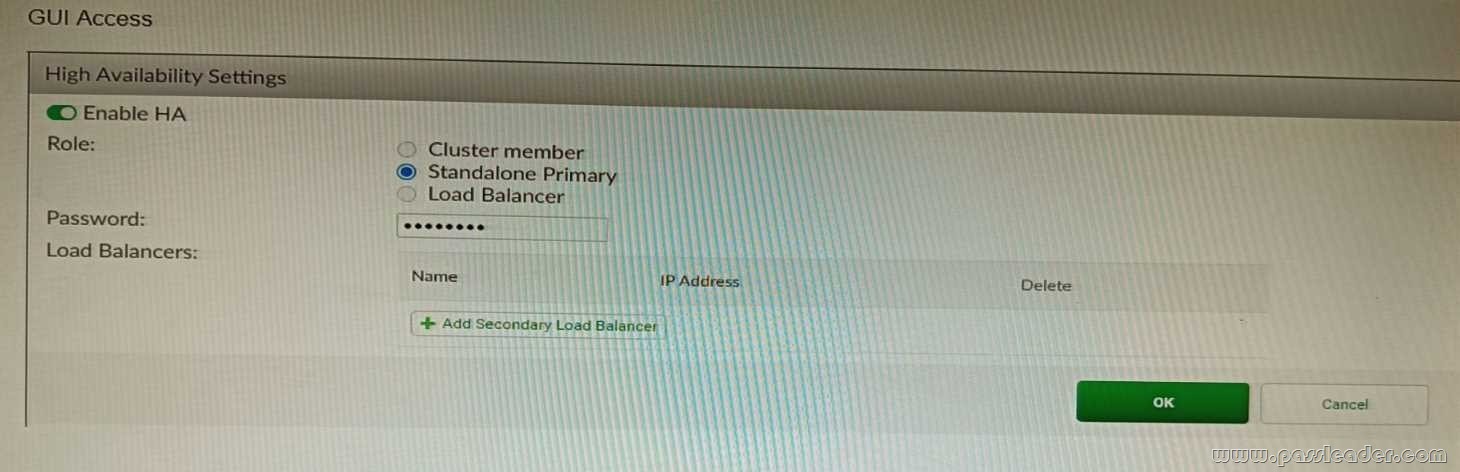
Based on this information, which statement is true about the next FortiAuthenticator (FAC2) member that will join an HA cluster with this FortiAuthenticator (FAC1)?
A. FAC2 can only process requests when FAC1 fails.
B. FAC2 can have its HA interface on a different network than FAC1.
C. The FortiToken license will need to be installed on the FAC2.
D. FSSO sessions from FAC1 will be synchronized to FAC2.
Answer: D
Explanation:
When FortiAuthenticator operates in cluster mode, it provides active-passive failover and synchronization of all configuration and data, including FSSO sessions, between the cluster members. Therefore, if FAC1 is the active unit and FAC2 is the standby unit, any FSSO sessions from FAC1 will be synchronized to FAC2. If FAC1 fails, FAC2 will take over the active role and continue to process the FSSO sessions.
https://docs.fortinet.com/document/fortiauthenticator/6.1.2/administration-guide/122076/high-availability
NEW QUESTION 16
Refer to the exhibits:

The exhibits show a FortiGate network topology and the output of the status of high availability on the FortiGate. Given this information, which statement is correct?
A. The ethertype values of the HA packets are 0x8890, 0x8891, and 0x8892.
B. The cluster mode can support a maximum of four (4) FortiGate VMs.
C. The cluster members are on the same network and the IP addresses were statically assigned.
D. FGVMEVLQOG33WM3D and FGVMEVGCJNHFYI4A share a virtual MAC address.
Answer: D
Explanation:
The output of the status of high availability on the FortiGate shows that the cluster mode is active- passive, which means that only one FortiGate unit is active at a time, while the other unit is in standby mode. The active unit handles all traffic and also sends HA heartbeat packets to monitor the standby unit. The standby unit becomes active if it stops receiving heartbeat packets from the active unit, or if it receives a higher priority from another cluster unit. In active-passive mode, all cluster units share a virtual MAC address for each interface, which is used as the source MAC address for all packets forwarded by the cluster.
https://docs.fortinet.com/document/fortigate/6.4.0/cookbook/103439/high-availability-with-two-fortigates
NEW QUESTION 17
Refer to the exhibit:
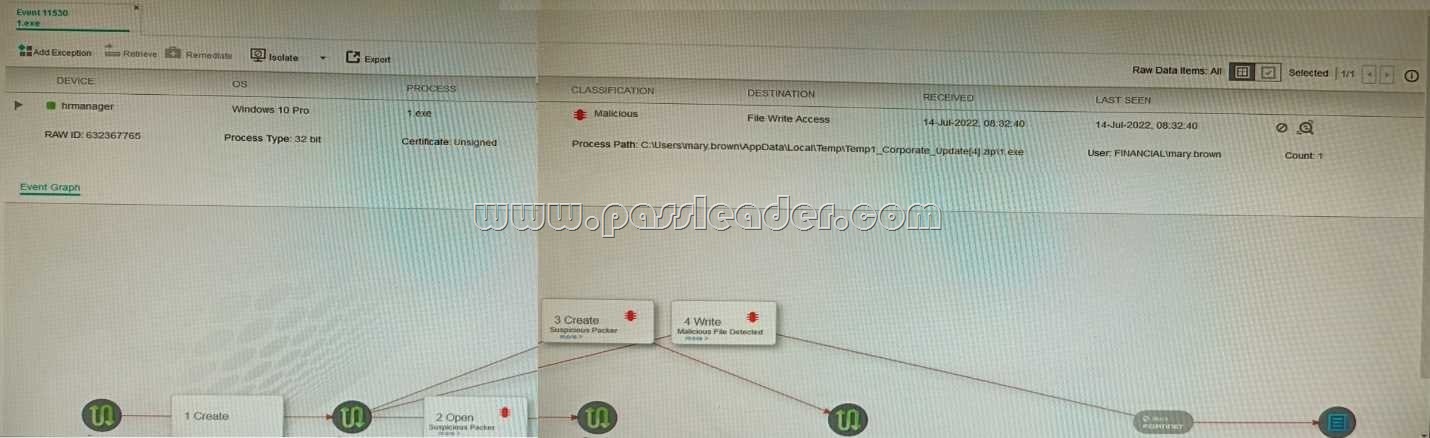
The exhibit shows the forensics analysis of an event detected by the FortiEDR core In this scenario, which statement is correct regarding the threat?
A. This is an exfiltration attack and has been stopped by FortiEDR.
B. This is an exfiltration attack and has not been stopped by FortiEDR.
C. This is a ransomware attack and has not been stopped by FortiEDR.
D. This is a ransomware attack and has been stopped by FortiEDR.
Answer: B
Explanation:
The exhibit shows that the FortiEDR core has detected an exfiltration attack. The attack is attempting to copy files from the device to an external location. The FortiEDR core has blocked the attack, and the files have not been exfiltrated. The exhibit also shows that the attack is using the Cobalt Strike beacon. Cobalt Strike is a penetration testing tool that can be used for both legitimate and malicious purposes. In this case, the Cobalt Strike beacon is being used to exfiltrate files from the device.
The other options are incorrect. Option A is incorrect because the attack has not been stopped. Option C is incorrect because the attack is not a ransomware attack. Option D is incorrect because the FortiEDR core has not stopped the attack.
https://docs.fortinet.com/document/fortiedr/6.0.0/administration-guide/733983/forensics
https://www.cobaltstrike.com/
NEW QUESTION 18
Refer to the exhibit, which shows a VPN topology:

The device IP 10.1.100.40 downloads a file from the FTP server IP 192.168.4.50. Referring to the exhibit, what will be the traffic flow behavior if ADVPN is configured in this environment?
A. All the session traffic will pass through the Hub.
B. The TCP port 21 must be allowed on the NAT Device2.
C. ADVPN is not supported when spokes are behind NAT.
D. Spoke1 will establish an ADVPN shortcut to Spoke2.
Answer: D
Explanation:
D is correct because Spoke1 will establish an ADVPN shortcut to Spoke2 when it detects that there is a demand for traffic between them.
https://community.fortinet.com/t5/FortiGate/Technical-Tip-Fortinet-Auto-Discovery-VPN-ADVPN/ta-p/195698
NEW QUESTION 19
……
Learning the PassLeader NSE8_812 dumps with VCE and PDF for 100% passing Fortinet certification — https://www.passleader.com/nse8-812.html (60 Q&As Dumps)
BONUS!!! Download part of PassLeader NSE8_812 dumps for free — https://drive.google.com/drive/folders/1We0_GwUcE8mOSEjEkLplImcGPBHV5qQa